There is a sea change occurring in data centers brought on by the relatively new technology of containers. Yet, as often happens with new technologies, security has taken a back seat. We caught up with James Scott, a Dell Technologies field CTO and CloudLink expert, to discuss all things container and security. “Just about every customer meeting involves a discussion on containers, and container orchestration,” James says, and “they’re trying to understand what it means to run, update, and secure a cluster.”
Now that containers are proving their value as transformative solutions for the data center, organizations are looking for ways to secure them. Simply securing your containers, though, isn’t enough. It’s important to see containers as an extension of the whole infrastructure, which means adopting a security strategy that covers the entire enterprise: bare-metal, virtual machines, cloud, and containers. Enter CloudLink 7.0.
Data security strategies were virtually non-existent in the early days of containers, resulting in many updates at the orchestration layer from bug fixes to new security-focused features. This led to spotty or inconsistent layers of security for organizations adopting containers. It doesn’t need to be that way.
Container Security doesn’t need to be in a vacuum
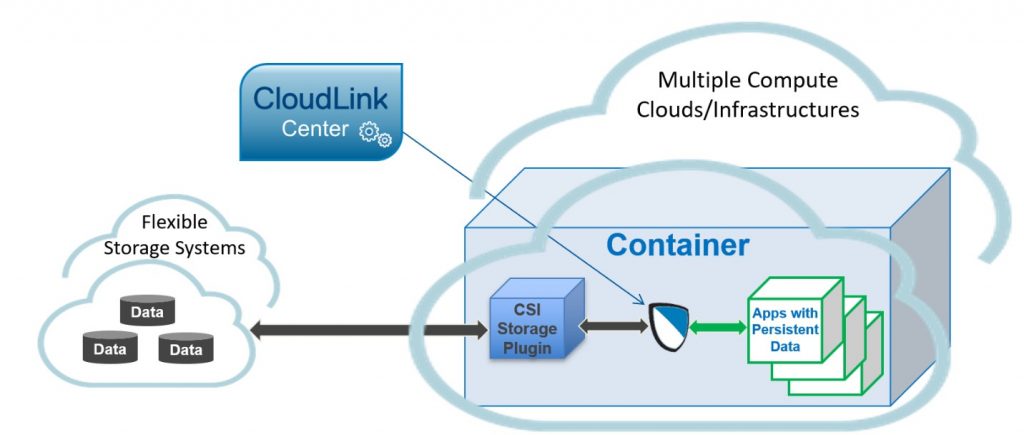
With the release of CloudLink 7.0, we introduce file volume encryption for Kubernetes container deployments. Given the extreme mobility of containers, keeping customer data safe as applications move throughout a deployment – especially within the cloud – is a challenge. Our container encryption functionality is built on the same agent-based encryption architectural model that we currently offer for virtual machines and VxFlex OS. We deploy an agent within the container that sits directly on the data path. As the data is saved, we intercept it and make sure it’s encrypted as it travels to, and then comes to rest in, the data store.
Container security doesn’t need to mean complex management
CloudLink makes data encryption and key management simple. When deployed, CloudLink’s agents will configure and enable data encryption as the customer needs it, providing full lifecycle key management. “That’s the beauty of our solution,” James says. “The CloudLink agent is deployed between the application and something called the CSI – Container Storage Interface.” CSI is a community developed standard that allows for different storage implementations to present the same interface to all applications so that no matter what type of storage is on the back end, any application can save its data. With CloudLink between the application and the CSI, we can be sure that all the data is encrypted as it is saved.
Broad storage support
At Dell Technologies, we have storage solutions that fit into the Kubernetes model for persistent storage. CloudLink is often implemented with our VxFlex storage platforms, and it can be used with other Dell storage or even third-party products. CloudLink can also act as a simple key manager for third party products, such as VMware’s native encryption. We do this over the Key Management Interoperability Protocol, aka KMIP, which is an open standard that governs the communication between encryptors and key managers.
Interested in CloudLink for your containers and beyond?
Our customers can reach out to their Dell Technologies sales representative who in turn can engage the CloudLink team for help. We’re always happy to chat with our customers directly to understand their environment and their data encryption needs. To support the sales teams, we have information and tools that they can use at our community site and recently updated web-based training for anyone interested, including our services teams and the customer themselves. We allow our customers to try CloudLink before they buy, which means all its functionality can be evaluated by downloading the binaries at our support site and obtaining an evaluation license from the sales team.