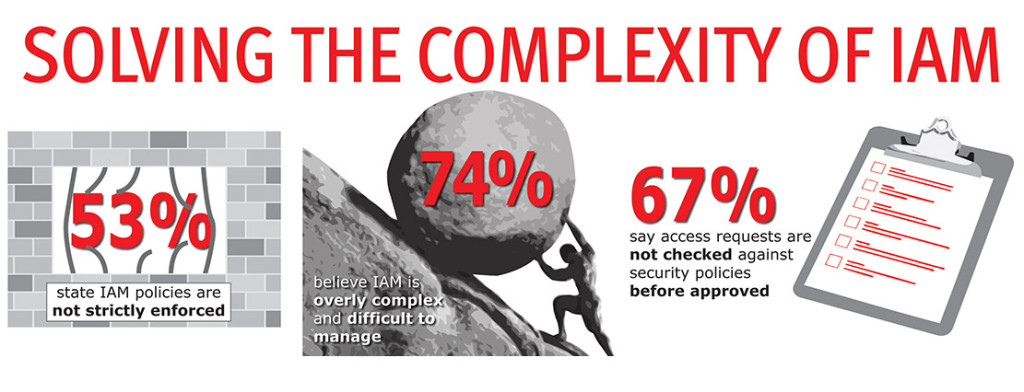
Information security has always been a complex beast, and this beast has visibly grown in both scale and scope over the past few years. From the perspective of Identity and Access Management (IAM), the number and type of information resources in play has risen exponentially, as have requests for user access to these resources. However, according to a recent Ponemon survey, most organizations are struggling to manage users’ access rights effectively and efficiently, and see IAM as being overly complex.
Given these challenges, the most recent release of the RSA Identity Management and Governance solution (Aveksa) is designed to focus simplifying this complexity, and giving our customers a way to deliver smarter IAM, rapidly, reliably, and cost-effectively. Let’s explore how we’ve pushed the envelope:
Role Management
Many organizations are eager to obtain the benefits of a role-based approach to access management, but are wary of the time and effort required. The good news is that we now provide a simple way to obtain many of the benefits of roles, without initiating a formal role management program. As managers go through the process of onboarding new users, the system will automatically suggest which entitlements should be granted based on patterns of entitlements for existing users. By intelligently suggesting entitlements, customers can deliver more appropriate and faster access, thus increasing user productivity without increasing risk.
“Off limits” Application Entitlements
Often, application owners must control which application entitlements users are permitted to obtain. Typically they do this by creating application roles, which are collections of entitlements bundled within roles defined inside of the application. These roles are the objects that users and managers should interact with, rather than the fine-grained entitlements that are embedded within them. Our new capabilities allow application owner to ensure that users can only obtain these application roles, and cannot directly obtain any “off-limits” entitlements. Again, we’re simplifying IAM for the user, while providing a better level of control for the administrators.
Provisioning from the Cloud
Finally, our new releases are engineered to include the capability to provision access changes regardless of where the solution is deployed. Today’s hybrid enterprises demand the flexibility to deploy solutions either on-premise or in the cloud, and our latest release embraces this. The RSA solution now provides support for the full identity lifecycle – including provisioning of both on-premise and cloud applications – whether deployed in a traditional on-premise manner, or as a cloud-based service.
The scale and complexity of today’s hybrid enterprises places a heavy burden on InfoSec teams, who are tasked with efficiently delivering access to business users without sacrificing security or compliance. In order to accomplish this, enterprises need a modern and capable IAM platform, which is engineered to simplify and streamline their business and technical processes.