Names can be confusing.
Whenever I see IT professionals interchangeably use cyber-resilient and cybersecurity, I am reminded of this famous line from Shakespeare’s immortal classic Romeo and Juliet:
“What’s in a name? That which we call a rose
By any other name shall smell just as sweet”.
However, there is a world of difference between cyber-resilient and cybersecurity.
For starters, cyber-resilience is a mindset. It is an approach to consider all the issues that occur before, during and after a system has encountered a threat or adverse event. It is an evolving perspective that essentially brings the areas of information security, business continuity and organizational resilience together. Cybersecurity has a narrower, technical focus and can be binary – either you have a lock on the door or you do not. Most businesses have basic cybersecurity measures to protect themselves but few are genuinely cyber-resilient.
Cyber-resiliency requires a longer-term, sustainable approach to business risk. Just focusing on IT security is no longer sufficient. Examples of businesses not being able to protect themselves from cyber threats or human error are numerous. For example, the 1 billion passwords stolen from Yahoo!, the WannaCry malware, the theft of thousands of sensitive employee information from the Department of Justice. Businesses must be able protect their assets, including data and people (from themselves and from others) as the cost of lost or stolen data can be crippling (see graph below).
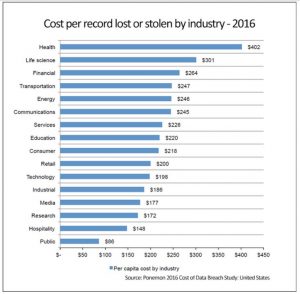
The fear of such large losses and associated disruption has motivated businesses to increase their investments and have a renewed focus in building a more secure, cyber-resilient business.
Enterprises are now thinking long and hard on how they choose infrastructure, people and processes because cyber-resilient initiatives are strategic and long-term in nature. To be effective, we believe cyber-resilient organizations need to make concerted efforts in three key phases: Protect, Detect and Restore
- Protect – create mechanisms and processes that will ensure authorized or authenticated access to critical systems and mitigate impact
- Detect – continuous monitoring, collection, verification and reporting of strange behavior
- Restore – mechanisms and processes to rapidly restore operations back to normal
These phases align with the five framework core functions recommended by the National Institute of Standards and Technology (NIST) in their Framework for Improving Critical Infrastructure Cybersecurity (Version 1.0) from February 12, 2014
Managing business risk is one of the key roles of senior management and they are including cyber risk as one of their top risks. Half the battle against a cyber-attack involves planning and preparing for potential threats and adverse outcomes. The next-generation business systems (software, applications, hardware) will incorporate the above three phases as an integral part of a cyber-resilient framework. Business systems designed and built with this framework offer better protection and are better prepared to deal with emerging cyber threats. Cyber-resiliency allows a business to return to normal operation more quickly through rapid detection and recovery in the event of a security incident.
Cyber-resilient initiatives cover more areas of a business than information-security initiatives. With the adoption of new trends and practices such as IoT, Opensource technologies, greater transparency and improved connectivity, the way we collect, store, move and use data has dramatically changed. It is vital for businesses to be cyber-resilient so they can protect themselves better, detect malicious intent faster and recover rapidly from cyber threats. As organizations become ever more connected and more complex, employing systems that are cyber-resilient are no longer a luxury but a necessity.
Yes, names can be confusing. In the case of cyber-resiliency vs. cybersecurity, it means a whole world of difference!
P.S. All Dell EMC PowerEdge servers are designed to be cyber-resilient. Visit DellEMC.com/servers to learn more.